Sunday, December 6, 2015
Some Antenna Measurements
I have been so swamped with work and family things...and some revisiting of old hobbies such as electronics and HAM Radio. So this post has really nothing to do with security, at the moment. I have been playing with some SDR's and researching some techniques and attacks from that standpoint.
Anyway, I'm having some pains with getting one of my quad-band radios to work and decided that I am going to just homebrew a new antenna. Since I needed the measurements, I figured I'd use Excel to handle the math.
The first chart is the measurements (based on the center frequency for each band) for the Driver and Radials for a Ground Plane antenna. I've double-checked most of the math, somewhat randomly, and I'm 99% certain is accurate.
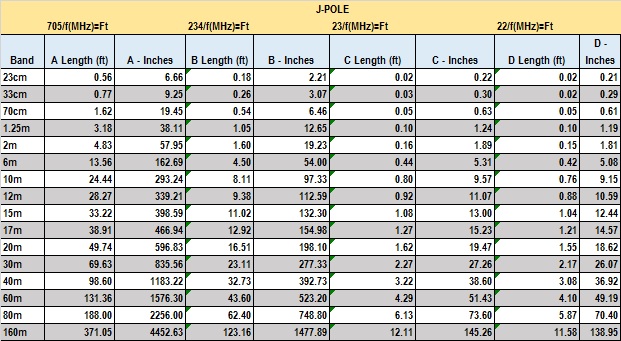
This chart is the measurements for a J-Pole antenna, based again on center frequency for each band. When I have more time I will be updating this with a better explanation and a generic drawing of a J-Pole antenna and how the different A, B, C, D measurements play a role. Suffice to say, the J-Pole antenna looks really cool to me and I think it would be awesome to build!
Unfortunately, I forgot to record where I got the bottom picture from so I'll have to find the appropriate site/person to credit when I get a minute.
Sunday, August 30, 2015
Windows 10 Update - Flickering pain
So I decided it would be a great idea to upgrade on my home machines to Windows 10. I had already updated my laptop and had had NO issues with it. Not so smoothly with my desktop.
What ended up happening was that as soon as I logged in, the screen would start to flicker, a lot, as in almost to the point of inducing migraines! After a few minutes digging, I found the below solution, and link.
Step 1: Open Task Manager. You can do this by hitting ctrl+alt+delete and selecting Task Manager from the list that appears
Step 2: In the top left corner, hit “File” and select “run new task” from the drop down menu.
Step 3: Type “msconfig” into the box.
Step 4: A new box will open. In this new box, select the Service tab.
Step 5: Scroll through the list and search for “problem reports and solutions control panel support” and “windows error report service.”
Step 6: Disable the two items by clicking the checked box beside them. The check should disappear.
Step 7: Click Apply, then click OK.
Step 8: You may be prompted to restart your computer. This is not necessary, but definitely recommended.
If your computer uses Norton Antivirus, upon restart, it will probably be a good idea to update the Norton program (hopefully the program will prompt you to update). If you do not use Norton, you still might want to run an antivirus scan and even perhaps an anti malware scan.
After that, your PC should be in good shape. Enjoy Windows 10! And remember, if you don’t like it, I’ve read that for a month you have the option to revert back to your old OS. If you want to, a quick internet search will bring up an easy step by step process (but remember to always back up your info before switching an OS!!).
Hope everything starts working again! Have a good night!
https://social.technet.microsoft.com/Forums/en-US/087c7f87-69e1-45eb-83d1-e92dfa497e99/windows-10-flashing-screen-after-upgrade-from-windows-7?forum=onlineservices
Peace out, YO!
What ended up happening was that as soon as I logged in, the screen would start to flicker, a lot, as in almost to the point of inducing migraines! After a few minutes digging, I found the below solution, and link.
Step 1: Open Task Manager. You can do this by hitting ctrl+alt+delete and selecting Task Manager from the list that appears
Step 2: In the top left corner, hit “File” and select “run new task” from the drop down menu.
Step 3: Type “msconfig” into the box.
Step 4: A new box will open. In this new box, select the Service tab.
Step 5: Scroll through the list and search for “problem reports and solutions control panel support” and “windows error report service.”
Step 6: Disable the two items by clicking the checked box beside them. The check should disappear.
Step 7: Click Apply, then click OK.
Step 8: You may be prompted to restart your computer. This is not necessary, but definitely recommended.
If your computer uses Norton Antivirus, upon restart, it will probably be a good idea to update the Norton program (hopefully the program will prompt you to update). If you do not use Norton, you still might want to run an antivirus scan and even perhaps an anti malware scan.
After that, your PC should be in good shape. Enjoy Windows 10! And remember, if you don’t like it, I’ve read that for a month you have the option to revert back to your old OS. If you want to, a quick internet search will bring up an easy step by step process (but remember to always back up your info before switching an OS!!).
Hope everything starts working again! Have a good night!
https://social.technet.microsoft.com/Forums/en-US/087c7f87-69e1-45eb-83d1-e92dfa497e99/windows-10-flashing-screen-after-upgrade-from-windows-7?forum=onlineservices
Peace out, YO!
Friday, July 31, 2015
Moving on in life, career
I had really thought that I would already be in bed sound asleep tonight after a busy day. Unfortunately, it is the 3rd of July, which comes directly after the 2nd of July, and directly before the 4th of July, which I am certain any 2nd grader could have told everyone. Anyway, it's around this time of year that at basically any time of the day or night, even here in West Bloomfield, that those wonderful mortar rounds start going...I mean fireworks. Fireworks to most people, and even to me sometimes...but also mortar, rocket, IED, etc. exploding all around. So...until I am not so...amped...up, I figured I'd watch a movie and write some stuff here. :-)
New Job, New Home, New Peoples, Old Family, Old Friends, Old Home!
In the last month we, my family and I, packed up house and trucks and headed north. Hopefully it's our next to last final one before we find some land and build a perfect Michigan Palace...and no, I don't meet a double-wide in Warren. OK...maybe a bad joke so a I'll add a heartfelt apology to the people in Warren, in trailers or otherwise.
Anyway, back to the move for a quick second. I learned a few very important lessons with this move, in both career terms and in taking care of our 'stuff.' I'll be happy to share these in a minute but first I think I might mention the reason for the move.
In August of 2014 we packed up our lives in Augusta, GA and headed for the 'DC Life,' with my job in Alexandria, contracting still for the Army (Northrop Grumman) as a Cyber Operator on the Army's Red Team. Now, I don't care what organization you are with or who you fantasize is the best 'Red Team' and techs. I will tell you that I'd be more than happy to go 'fist to cuffs' with anyone who doesn't agree that the Cyber Operators on the Army's Red Team have been the best, have trained some of the best', and have proven this time and again. Anyway, I digress.
Although we moved there in August of 2014 and I felt like I was a part of the team from the get-go, it was also a contract re-bid year for what I assume is at least 80% the DoD. This meant that a lot of good people on the team received some very good offers to move on. So, I still loved the time I spent there and there really are some excellent operators sitting there now. But with the composition changing so much and some frustration my wife was having with her own job as a teacher, she said she was ready to go.
I came across, on a whimsical look at indeed.com, a posting for a CyberSecurity guy/gal...and it was in Auburn Hills, MI with Fiat Chrysler Automobiles.I applied, interviewed, felt I blew it but they still flew me up for a panel interview which I knew I blew. Then I got THE Offer. The kind of offer a mid-career techie like me loves to get. Small team, individual's with particular areas of focus, such as Vehicular Network Penetration Testing (MINE!!!), great money (for a guy who's not really greedy anyway, AND the FULL relocation package with free realtors, movers, packers, etc. Oh, and the benefits are OUTSTANDING. Most importantly, the people I am working with directly and tangentially are pretty AWESOME.
So, I have been at FCA for two weeks now and am having a blast. About my only complaint is that I need to get a corporate leash (at least I got to pick a Droid) :-) Seriously though I love it. I have been inundated with new project assignments, taking over other projects, and just digging chest-deep into new protocols and tactics!
New Job, New Home, New Peoples, Old Family, Old Friends, Old Home!
In the last month we, my family and I, packed up house and trucks and headed north. Hopefully it's our next to last final one before we find some land and build a perfect Michigan Palace...and no, I don't meet a double-wide in Warren. OK...maybe a bad joke so a I'll add a heartfelt apology to the people in Warren, in trailers or otherwise.
Anyway, back to the move for a quick second. I learned a few very important lessons with this move, in both career terms and in taking care of our 'stuff.' I'll be happy to share these in a minute but first I think I might mention the reason for the move.
In August of 2014 we packed up our lives in Augusta, GA and headed for the 'DC Life,' with my job in Alexandria, contracting still for the Army (Northrop Grumman) as a Cyber Operator on the Army's Red Team. Now, I don't care what organization you are with or who you fantasize is the best 'Red Team' and techs. I will tell you that I'd be more than happy to go 'fist to cuffs' with anyone who doesn't agree that the Cyber Operators on the Army's Red Team have been the best, have trained some of the best', and have proven this time and again. Anyway, I digress.
Although we moved there in August of 2014 and I felt like I was a part of the team from the get-go, it was also a contract re-bid year for what I assume is at least 80% the DoD. This meant that a lot of good people on the team received some very good offers to move on. So, I still loved the time I spent there and there really are some excellent operators sitting there now. But with the composition changing so much and some frustration my wife was having with her own job as a teacher, she said she was ready to go.
I came across, on a whimsical look at indeed.com, a posting for a CyberSecurity guy/gal...and it was in Auburn Hills, MI with Fiat Chrysler Automobiles.I applied, interviewed, felt I blew it but they still flew me up for a panel interview which I knew I blew. Then I got THE Offer. The kind of offer a mid-career techie like me loves to get. Small team, individual's with particular areas of focus, such as Vehicular Network Penetration Testing (MINE!!!), great money (for a guy who's not really greedy anyway, AND the FULL relocation package with free realtors, movers, packers, etc. Oh, and the benefits are OUTSTANDING. Most importantly, the people I am working with directly and tangentially are pretty AWESOME.
So, I have been at FCA for two weeks now and am having a blast. About my only complaint is that I need to get a corporate leash (at least I got to pick a Droid) :-) Seriously though I love it. I have been inundated with new project assignments, taking over other projects, and just digging chest-deep into new protocols and tactics!
Thursday, March 12, 2015
Describing SSH to your mother
I was recently asked how I would describe SSH to the person's mother. Assuming that English is her native tongue, I gave the first explanation that came to mind. This explanation involved the use of puzzle pieces and colorful napkins. I originally didn't plan to to rehash that here. Instead, I thought I would refresh myself on the protocol (SSH 2.0) and write it up...so it's maybe fresher in my mind as it has admittedly been quite a while since I have gotten into the nuts and bolts of SSH. I think I will do a little of both. :-) To keep it simple (I hope) I will first discuss SSH from the more nerdy side of life and will break the discussion into
The Players:
CLIENT
SERVER
Switch 1 (just be cognizant that my discussion here involves communication between the CLIENT and SERVER using Switch 1)
Initial Session Setup
First, the same old three-way handshake.
CLIENT sends the SYN packet to SERVER
SERVER sends the SYN,ACK packet to CLIENT
CLIENT sends the final ACK packet of the handshake to SERVER
| Figure 1: TCP Handshake |
[RFC4523:4.2]
Protocol Version Exchange
Once the initial TCP-Handshake is accomplished, both Hosts announce to each other what protocol version they are running. This is known as the identification string and has the following format:
SSH-protoversion-softwareversion SP comments CR LF
| Figure 2: SSH Protocol Version Exchange |
SSH = should be obvious...but if not...try Basic Protocol Help
-protoversion = If this doesn't say 2.0 from the server, I'd avoid connecting...just sayin'
-softwareversion = No real concrete value. Basically, if it conforms to the applicable RFC's, it's fair game.
SP = literally, a SPACE character (ASCII 32)...NOT A NULL!!! This is ONLY needed if there are comments
comments - the identification string has a max length of 255. This section can be arbitrary but it is usually used by the server (again, SERVER in this case) to initiate the Diffie-Hellman key exchange.
- a few other quick notes:
-protoversion = must contain only printable US-ASCII characters with the exception of the minus sign and spaces
-softwareversion = "used to trigger compatibility extensions and to indicate the capabilities of an implementation" (RFC4253)
-comments = this should be used to provide helpful information to the user(s).
- There can be multiple lines sent by the client or server as long as:
- ONLY the first line starts with "SSH"
- each line MUST end with a Carriage Return(
[RFC4253:8]
 |
| Figure 3: DH Key Exchange |
Encrypted Traffic
Once the protocol is agreed upon and the key exchange is completed, the traffic is then encrypted. The key used for encryption can be changed during the conversation.
 |
| Figure 4: Encrypted SSH Traffic and Session Teardown |
Misc Notes
It is germane to note that the RFC defines additional, individual, items that can be used:
- The servery key_algorithm, the encryption_algorithm, and the mac_algorithm are required by the RFC to be a match between the Servers options and the FIRST matching option from the Client's list.
- MAC: Message Authentication Code, if its usage is agreed upon then each binary packet except the first will contain the MAC as the last field in the payload.
- compression: compression can be used when agreed upon by both the server and client. The RFC provides an interesting discussion in packet size and compression and how this may/may not affect network traffic.
- Key Change: a key change may be initiated by either side by sending a SSH_MSG_KEXINIT. The RFC does stipulate that the roles MUST NOT be changed, regardless of who initiates the key change process.
Now, back to telling your mother about SSH.
The Players:
Yourself (Client)
Your Mom(Server)
Puzzle Pieces
Different Color Napkins
Initial Session Setup
You know that you need to give your mother some puzzle pieces. However, the wind is blowing fiercely, the rain is pellting you both, and you must pass the pieces to your mother over a large crater between the both of you. So...
You call out to your mother: "Yo!"
Your Mom hollers back: "Yo, I can hear you!"
To which you holler: "I can hear you!"
Protocol Version Exchange
You mother lets you know that she can work with pieces from the 5000pc puzzle depicting the 1984 Detroit Tigers.
You have pieces for this puzzle and therefore let her know that this will work well for you.
Diffie-Hellman Key Exchange
Your mother now lets you know that she can use the puzzle pieces from your left and right jeans pockets and from your left coat pockets.
Your mother also lets you know that she can accept the pieces wrapped in Blue, Maize, or Orange.
You let your mother know that you do, in fact, have puzzle pieces in your left jeans pocket and in your left and right coat pockets.
You also let her know that you have the ability to use Maize or Orange colored Napkins.
Because you first mentioned the left jeans pocket and your mother can use this, these are the pieces you will be passing to your mother. Likewise, because you first listed the Maize colored napkins, the pieces will be wrapped with said napkins, as will any response from your mother.
Encrypted Traffic
Completing this puzzle is important to you. As such, you've contacted your mother, agreed upon which type of pieces are needed, and how to protect said pieces from the wind and rain. After you've agreed upon the pieces and the protection, there is no need for you to yell across the hole between the two of you.
So, I hope that this post will make sense to me in a year, and to anyone else who may read it. I left out some of the more technical things on purpose, especially the under-workings of the Diffie-Hellman protocol.
Subscribe to:
Posts (Atom)